Android Telegram Users at Risk: EvilLoader Vulnerability Still Unpatched

An independent cybersecurity researcher, operating under the pseudonym 0x6rss, has uncovered a critical vulnerability in the Telegram messenger for Android. This flaw allows attackers to disguise malicious applications as regular videos.
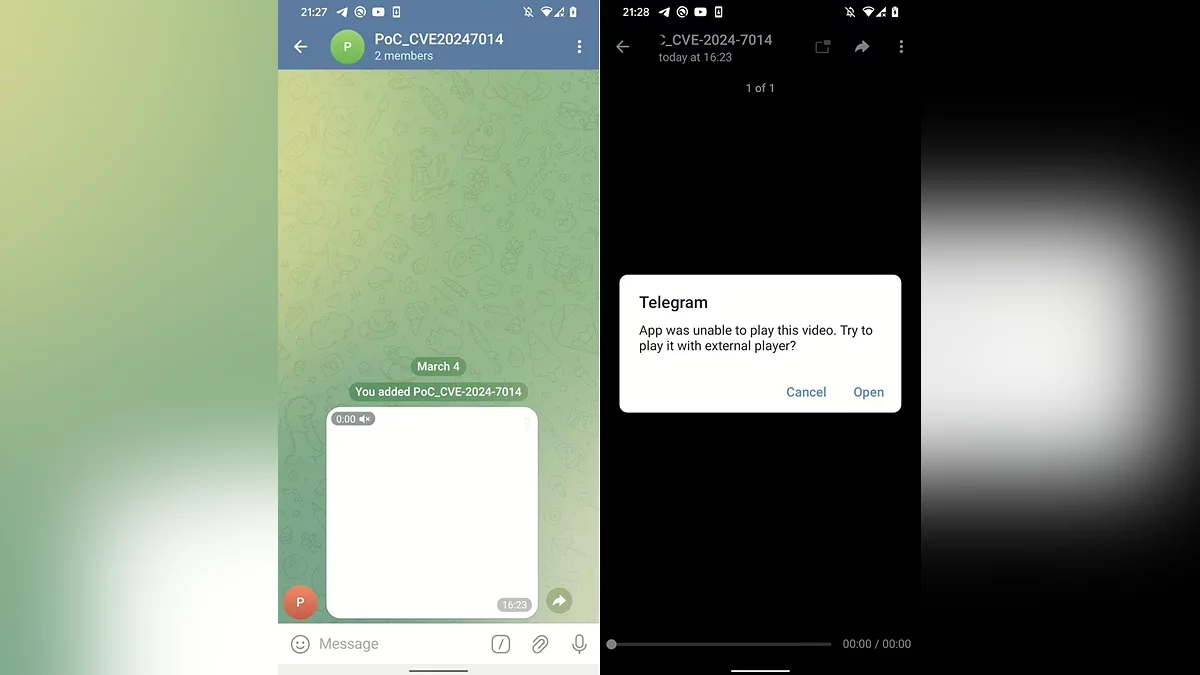
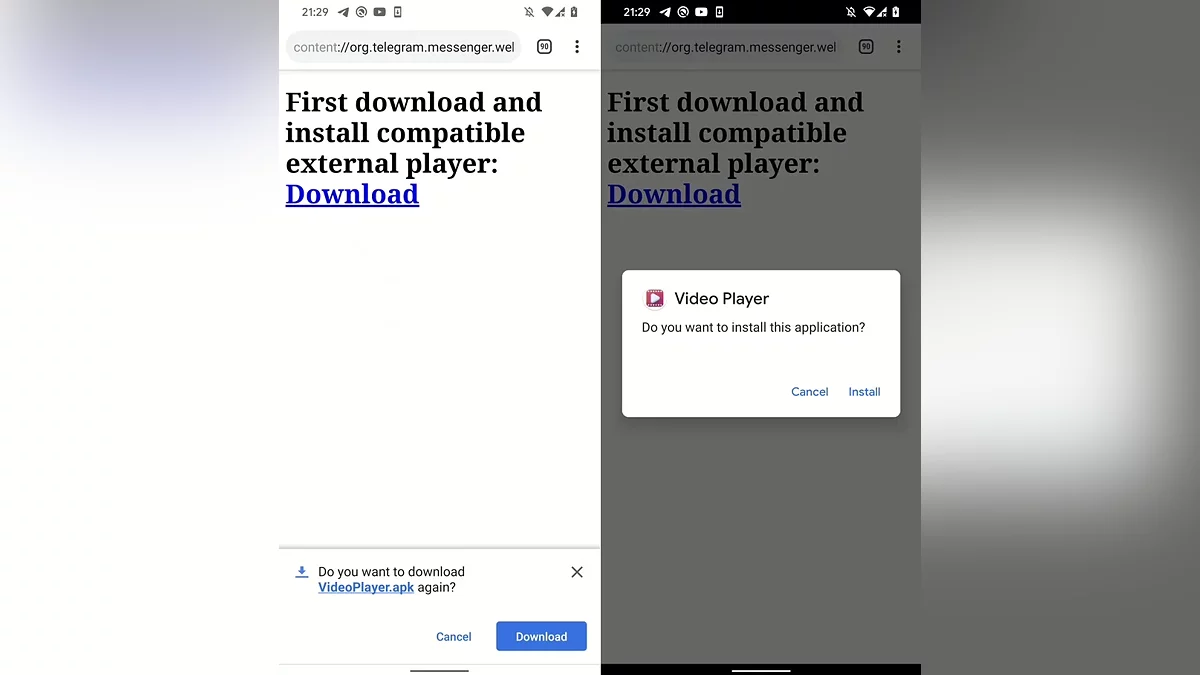
Attackers create fake HTML files that Telegram mistakenly recognizes as videos (with an .mp4 extension). When such a file is sent to a chat, it appears as media content. When a user attempts to open it, the messenger prompts them to install an external player. If the user agrees, a malicious APK file is downloaded onto the device, capable of stealing data or installing spyware.
It’s important to note that successful installation requires the victim to manually enable the installation of apps from unknown sources in their Android settings. However, as practice shows, many users are unaware of the risks and grant such permissions, especially if the file comes from a trusted contact.
This is the second incident of its kind this year. In July 2024, the EvilVideo vulnerability (CVE-2024-7014) was discovered, operating under a similar scheme. Both exploits have been actively sold on shadow forums, increasing the scale of potential attacks.
As of the publication of this news, Telegram representatives have not provided any official comments. A patch is expected to be released in the coming weeks, but until then, the threat remains critical for the 800 million users of the Android version of the app.
-
Intel Claims AMD and NVIDIA Put Users at Risk Due to Unpatched Vulnerabilities
-
Android 16 Arrives in June, Driven by a Development Revolution
-
KYC Nightmare. What Is SumSub and Why Users Say It Is Blocking Their Money on Crypto Platforms and Telegram (updated)
-
Hackers Attacked Bybit Crypto Exchange, Stealing Around $1.4 Billion
-
Cybersecurity Experts Call for DeepSeek to Be Removed from iPhones Due to Vulnerabilities